Welcome Summer with New Updates from NoTouch OS
As we embrace the sunny month of June and the arrival of summer in the northern hemisphere, we are thrilled to introduce NoTouch OS 3.6.0, a significant release packed with exciting new features, enhancements, and updates. To ensure you stay at the forefront of innovation, we highly recommend upgrading to version 3.6.65, which includes essential updates for the Citrix Workspace App and the Horizon client and is now GA.
NoTouch OS 3.6.0
New Features
- Citrix: Update Citrix Workspace App to 2405 (24.5.0.76)
- VMware Horizon: Update VMware Horizon View client to 2312.1-8.12.1-23543969
- Support IPP and IPP Everywhere printing
- Support Local Network Printer Auto-discovery
- Introduce Linux kernel 6.5 – k605 images (EXPERIMENTAL)
- ZScaler side-loadable (EXPERIMENTAL)
- Azure Virtual Desktop/Windows 365: FabulaTech USB redirection plugin support (EXPERIMENTAL)
- Azure Virtual Desktop/Windows 365: Add ControlUp RemoteDX plugin support (EXPERIMENTAL)
- Azure Virtual Desktop/Windows 365: Add DeviceTrust plugin support (EXPERIMENTAL)
- Citrix: Add ControlUp RemoteDX plugin support
- VMware Horizon: Add ControlUp RemoteDX plugin support
For detailed guidance on setting up our Control Up integration, dive into our blog for a step-by-step walkthrough on configuration.
Updates
- Update PuTTY to 0.81
- Update Dropbear to 2024.84
- Update BeyondTrust RS loader (formerly Bomgar) to support the latest agents
- Update ControlUp EdgeDX to 2.12.10.2323
- Teradici PCoIP (now HP Anyware): Update HP Anyware (formerly Teradici) PCoIP client to 24.03.3
- FreeRDP: Update FreeRDP 3 to 3cf4bac0e8
- FreeRDP: Update FreeRDP 2 to cb90fac074
- Azure Virtual Desktop/Windows 365: Plugin loader improvements
- ControlUp RemoteDX RDP/AVD plugin sideloadable
- Improve the readability of the shadowing consent message
- Imprivata: Imprivata helpers for RDS/RDP: Support .rdp files
- Microsoft Surface builds: Switch to kernel 6.9 (k609s)
Improvements
- Citrix: Support Citrix App Protection
- Citrix: Add parameter for ClientPrinterList
- OpenSSL parameters to connect to legacy (unsafe) servers if desired
- Inform user in case OpenH264 would be necessary, but couldn’t be downloaded
- GNUTLS update
- Add Open-VM-Tools
- Update CUPS
- Integrate Avahi
- New Dizzion-Frame icon
- Explicitly show IPP printer option
- Add several more kernel driver modules to k608
- Kernels k605 and k608 use Digimend 12
- Update OpenConnect to 9.12
- Remove serial port from VMX file (avoids annoying warning)
- Activate NEON for FreeRDP 2
- Various OS base tools update
- Update Node.JS environment
- Add ControlUp EdgeDX [arm64]
- Leostream: Add preconfigured credential support to Leostream
- Azure Virtual Desktop/Windows 365: Update Authentication dialog infrastructure
- Azure Virtual Desktop/Windows 365: Add custom certificates to sign-in browser
- Azure Virtual Desktop/Windows 365: Improve audio playback
- Azure Virtual Desktop/Windows 365: 3rd-party App Id support
- Azure Virtual Desktop/Windows 365: Username/password flow support
- Azure Virtual Desktop/Windows 365: Local configuration displays custom parameters nicer
- Azure Virtual Desktop/Windows 365: Printer auto-connect for configured CUPS printers
- HP Anyware (formerly Teradici PCoIP): Harden HP Anyware URL handling
- Add VM SCSI kernel modules
- Fancydownload: Show fewer dots in wget progress
- Azure Virtual Desktop/Windows 365: Plugin loader improvements
- ControlUp RemoteDX RDP/AVD plugin sideloadable
- Improve the readability of the shadowing consent message
- Imprivata: Imprivata helpers for RDS/RDP: Support .rdp files
- Microsoft Surface builds: Switch to kernel 6.9 (k609s)
I wanted to bring attention to the AVD improvements that streamline the auto-launching of applications easier than ever. Let’s look at how this is configured. In the example below I’m logged into our AVD environment, and I’ve highlighted Win1123H2 (Resource) and SessionDesktop (Published Desktop).
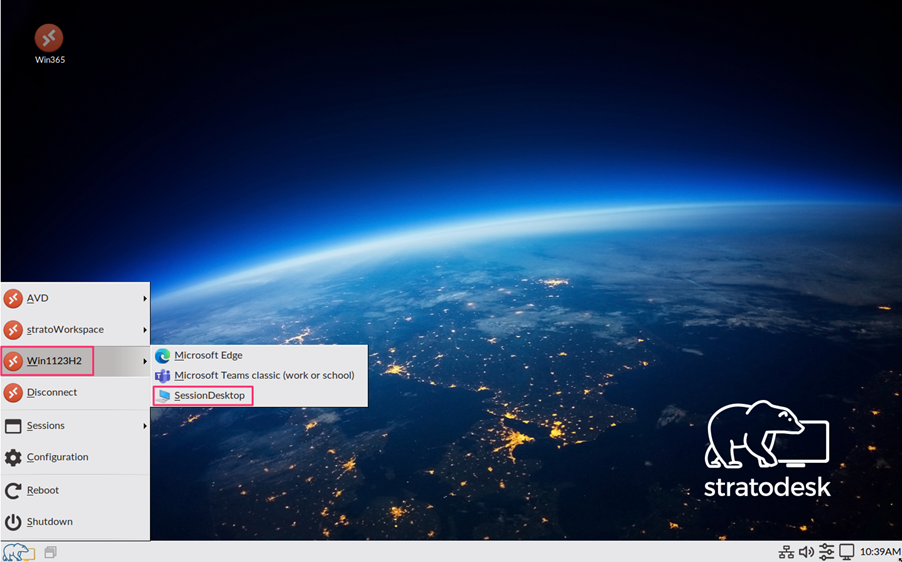
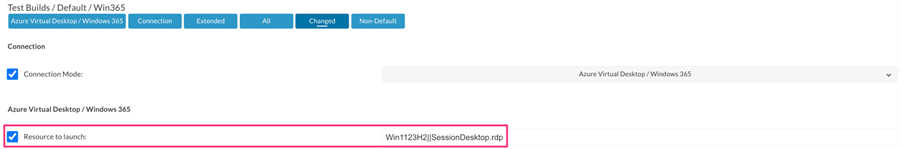
In the ‘Azure Virtual Desktop/Windows 365’ settings of your connection you need to configure the ‘Resource to launch’ parameter with Workspace||Resourcefile.rdp so in my case Win1123H2||SessionDesktop.rdp but please note that this is case sensitive, and if not correct then the published application or desktop will not launch.
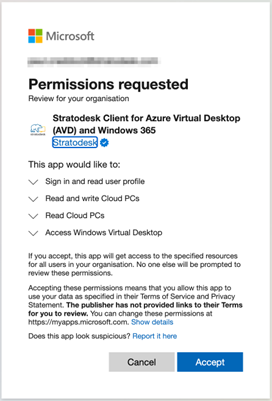
In some circumstances, it might be necessary to automatically log into a published resource where a device might not be easily accessible to enable a user to log in with a keyboard and mouse. Previously this has not been possible due to the way Microsoft requires an interactive login. We’re pleased to announce that this now is possible but some administrative steps need to be completed first to grant access to our AVD/Win365 client to your environment.
Further guidance can be found in the following article from Microsoft. However, in a nutshell, you need to grant tenant-wide admin consent URL in the following format:
https://login.microsoftonline.com/{organization}/adminconsent?client_id={client-id}
- {client-id} is the application’s client ID (also known as app ID).
- {organization} is the tenant ID or any verified domain name of the tenant you want to consent to the application.
The Stratodesk client/app-id is: 6febedc3-7ad3-4225-802b-2f9ca2e759c7
Once the full URL is entered into a browser by an Azure admin, you’ll be asked to confirm the permissions. Please note that this only needs to be done once for each tenant ID.
From a NoTouch Center perspective, you’ll need to be running 4.5.582 or later for some of the new parameters to be available.
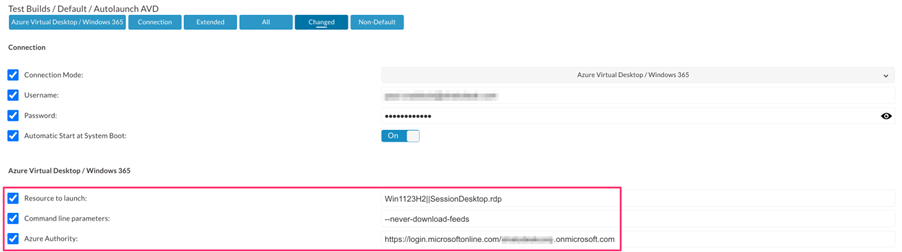
The ‘Azure Authority’ parameter is essentially the URL you would use if connecting via a web browser. Based on the parameters above a NoTouch OS endpoint will automatically start the AVD connection, log the user in, and launch my published Windows 11 (SessionDesktop) without the need for user interaction.
We’d only recommend automatic login in certain use cases as this could create a security risk.
Fixed Issues
- Fix OpenH264 download in first-boot-after-install or reset scenario
- Citrix: Fix a Workspace App sideloading issue
- Azure Virtual Desktop/Windows 365: Fix AVD client startup issue [Raspberry Pi]
Use k608s for Surface devices, k608 without the “s” is the 6.8 kernel for other devices that like 6.8.
NoTouch Center 4.5.585
Improvements
- Sync parameters with OS
- Add parametrization for Strict-Transport-Security
- More log cleanups
Fixed Issues
- Fix Firefox Kiosk parameter
If you’re looking to upgrade to the latest versions and are currently covered by maintenance, simply login to your customer portal. For any help with downloading, accessing your account, managing your subscription, or any other inquiries, don’t hesitate to reach out to our support team.
If you are not a customer yet and are interested in testing the software please reach out to us or fill out a trial request.
