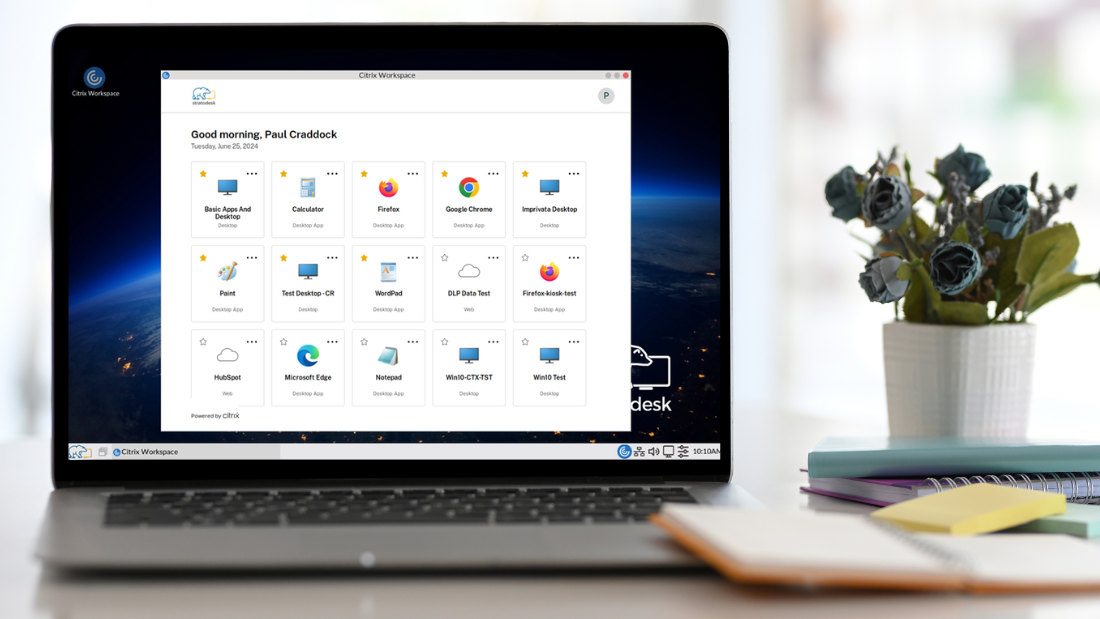
We are pleased to announce that we got early access to the Citrix Enterprise Browser (CEB) and are continuing our testing efforts in collaboration with Citrix.
The Citrix Enterprise Browser will officially become available soon. This is a highly anticipated product launch for Stratodesk customers and partners.
Though the Citrix Enterprise Browser is not yet available in Stratodesk NoTouch, we want to provide a preview of what’s coming in a future release.
What is Citrix Enterprise Browser?
Citrix Enterprise Browser is a Zero Trust Network Access (ZTNA) solution that helps reduce increasing cyber threats like phishing and data breaches due to overprivileged access and security gaps.
With the browser, you can also prevent data leakage, get observability across different personas with visibility and governance, and enforce Zero Trust Access for all apps. Let’s look at each of these in detail.
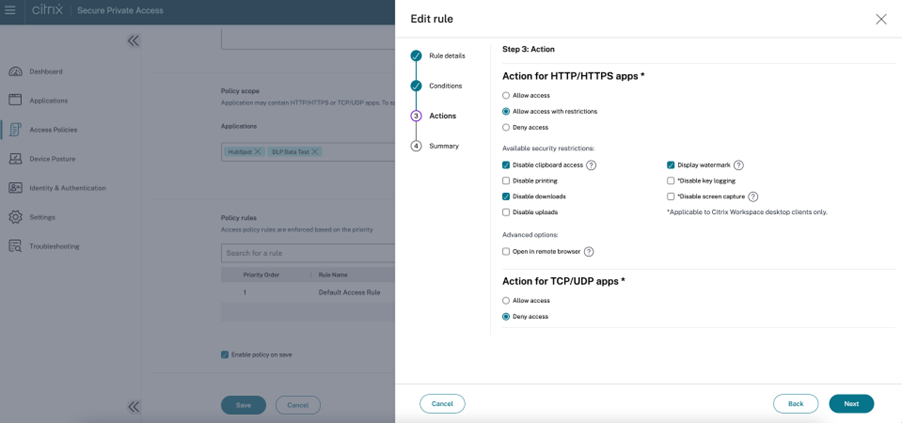
Data leakage prevention: You can enforce security controls like clipboard restrictions, download/upload/printing restrictions, and display watermarks to your web and SaaS apps.
- Clipboard restriction: Disables cut, copy, and paste operations between the app and the endpoint’s clipboard.
- Download restriction: Disables the ability to download from web and SaaS apps or copy files from the browser.
- Upload restriction: Disables the ability to upload files.
- Printing restriction: Disables the ability to print from within the app.
App Protection
NoTouch OS is an exceptionally secure operating system, and almost no interaction happens between an application inside the user’s desktop and NoTouch OS. For organizations running a local browser, the interaction runs locally on the machine and executes code locally.
Although NoTouch has several mechanisms in place to prevent permanent changes made by the user or malicious software loaded by the user, the possibility remains that users try to download and install Linux-based malware, spyware, or key loggers.
The Citrix Enterprise Browser, natively running on the client machine, can mitigate these threats by preventing such tools from accessing and reading sensitive data.
- Restrict keylogging: Scrambles a user’s keyboard inputs from keyloggers while accessing the web applications in the enterprise browser on Linux.
- Restrict screen capturing: Prevents anyone from taking screenshots or recording your screen using built-in solutions while using the app.
What does this look like from a user’s perspective? After authentication, users will see the desktops and applications they have access to.
Once the application is launched—let’s say HubSpot using the Enterprise Browser—the first thing you’ll notice is a watermark displaying your username and IP address. An administrator can choose to configure the watermark feature as an added security measure. The watermark prevents users from taking a picture with a mobile phone and sharing unauthorized information because the image can be traced back to the user.
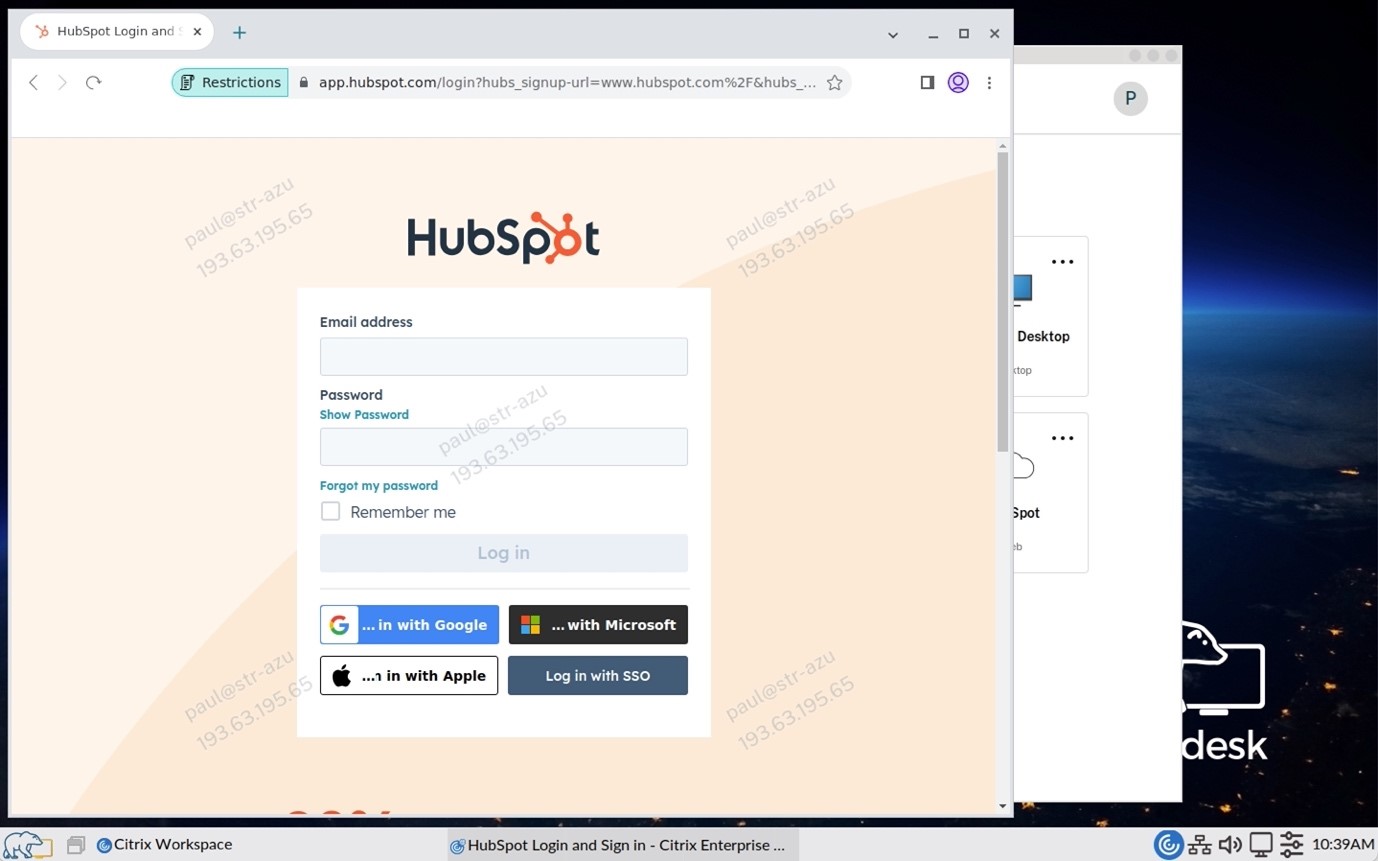
Next let’s look at the restrictions that are in place, which correspond with the current policy.
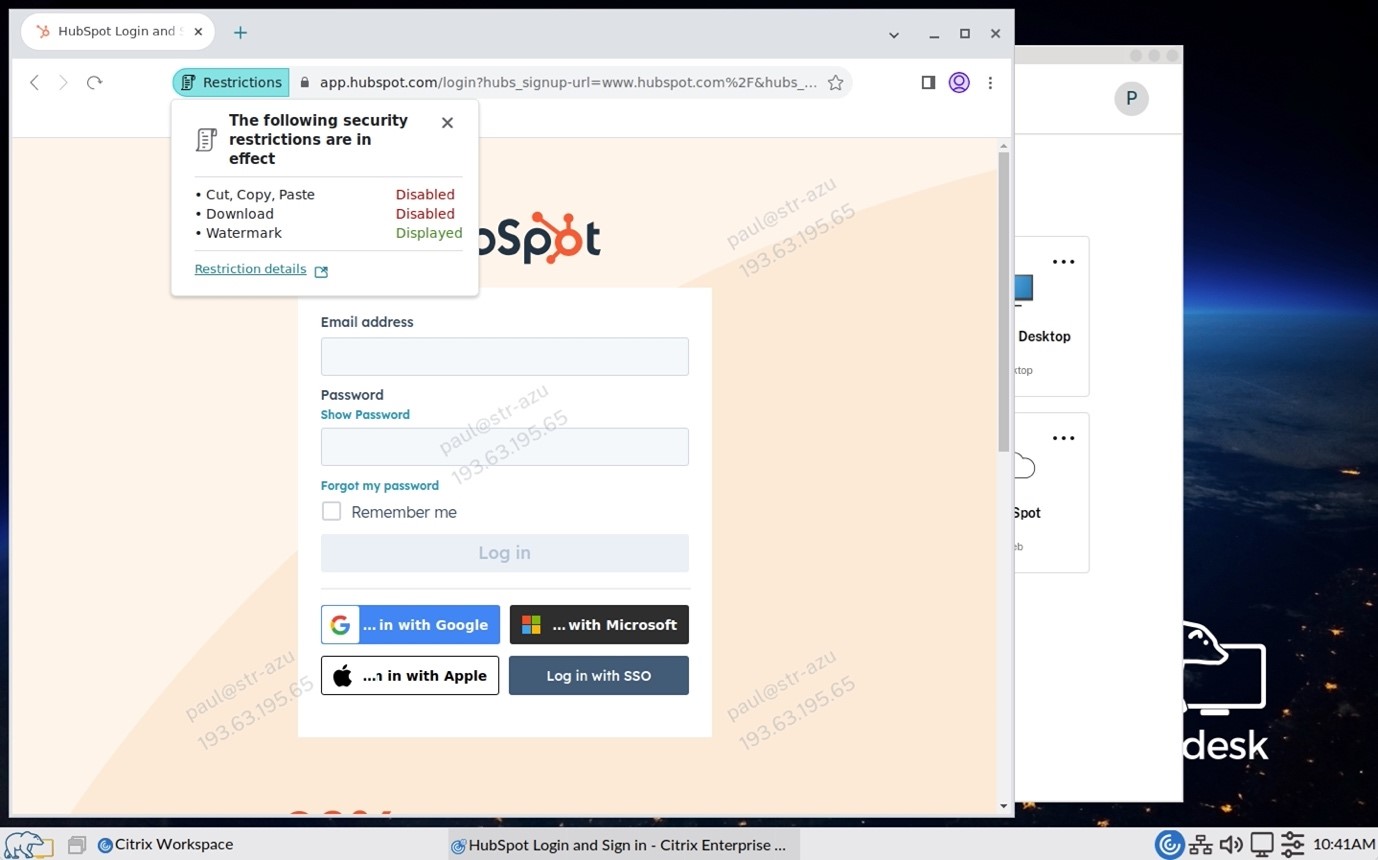
This will help the end user identify what restrictions are in place.
Protection from web threats: Web threat security for work becomes more critical, especially on unmanaged devices like contractor devices or employees’ BYO devices. Citrix Enterprise Browser has built-in last-mile web threat security.
Zero Trust Network Access: Citrix enterprise Browser is seamlessly integrated with ‘Citrix Secure Private Access’ providing VPNless contextual access to all internal web and SaaS applications, without the need for any agent on the device.
Observability: Achieve comprehensive visibility and governance over Citrix Enterprise Browser usage within your organization, enabling effective issue triage and seamless integration of browsing data with your preferred SIEM solution.
Conclusion
Citrix Enterprise Browser and Zero Trust Network Access enhance data security for both web and SaaS-based applications. Securing the attack surface is paramount for Stratodesk and Citrix and although this feature is still in technical preview, and the exact GA release date is unknown, we will continue to collaborate with Citrix on its implementation and testing.
Keep an eye on our LinkedIn or X (Twitter) channels for future updates. Request a free trial and start your journey today!