With the introduction of NoTouch Center version 4.5.1, Stratodesk is bringing MFA support to NoTouch Center to make the solution even more secure than it is already. The main driver behind this is the increased security threats that can be unintentionally introduced by employees, malware, or keylogging software that might steal passwords, etc. We are also seeing a large number of customers looking to deploy NoTouch Center in their own public cloud platforms like Microsoft Azure, Amazon Web Services, or Google Cloud and need extra layers of security when it comes to user authentication.
What MFA Methods are Supported?
NoTouch Center will support SMS via Twilio, email & TOTP via authentication apps from Microsoft, and Google which we used in our tests but others with the ability to scan a QR code should also work and can be set on a per-user basis.
TOTP MFA
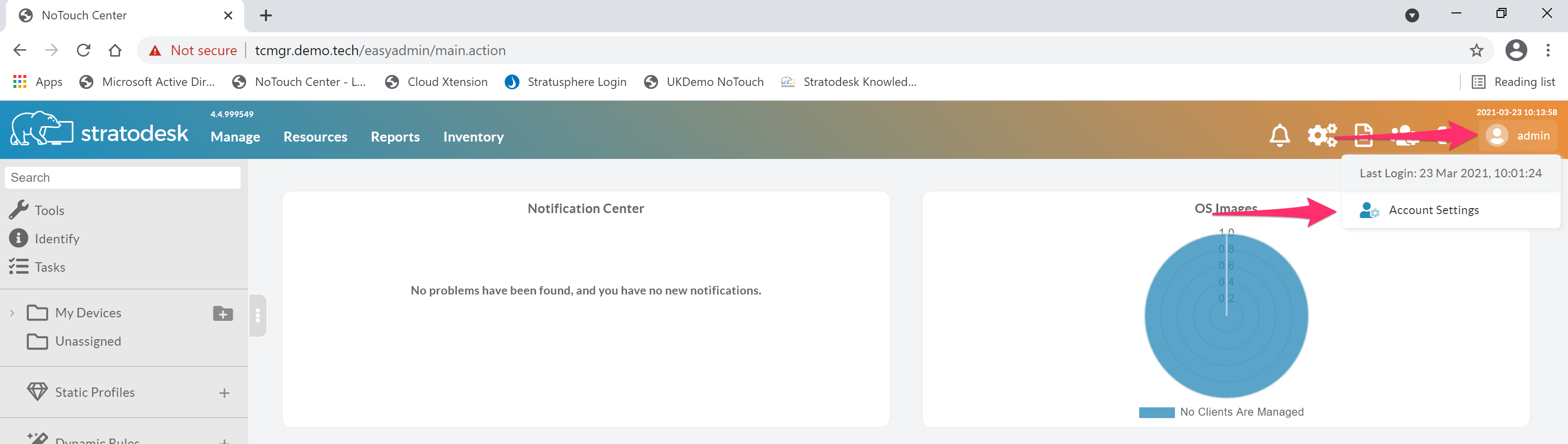
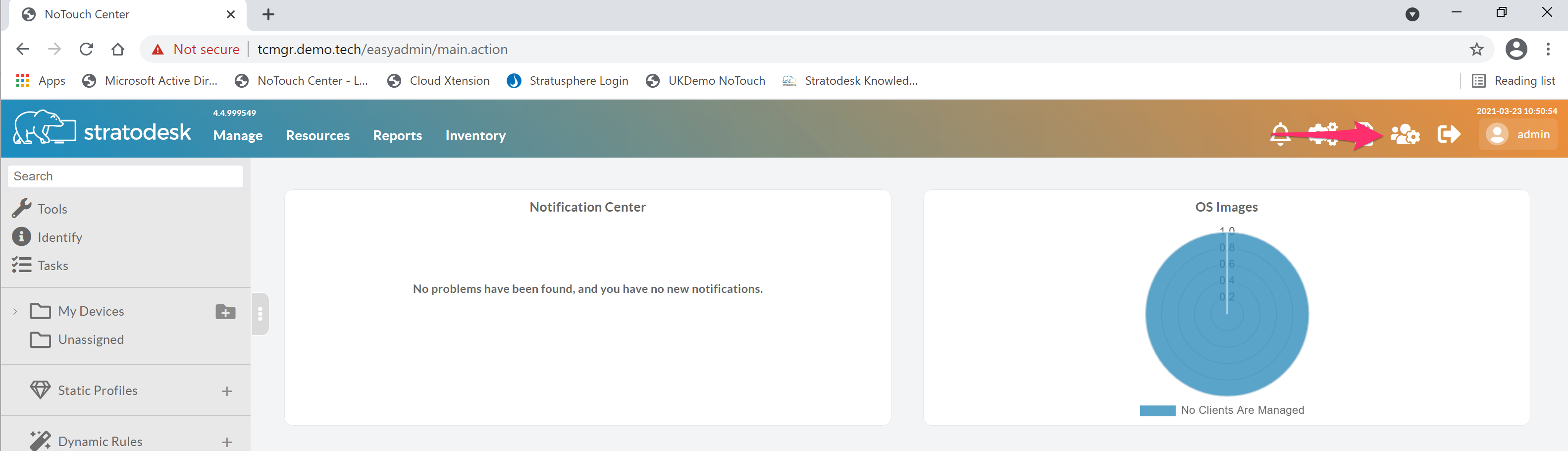
To enable TOTP MFA for the default ‘admin’ account, first select the user in the top right-hand side of the screen, and then select ‘Account Settings’ as shown below.
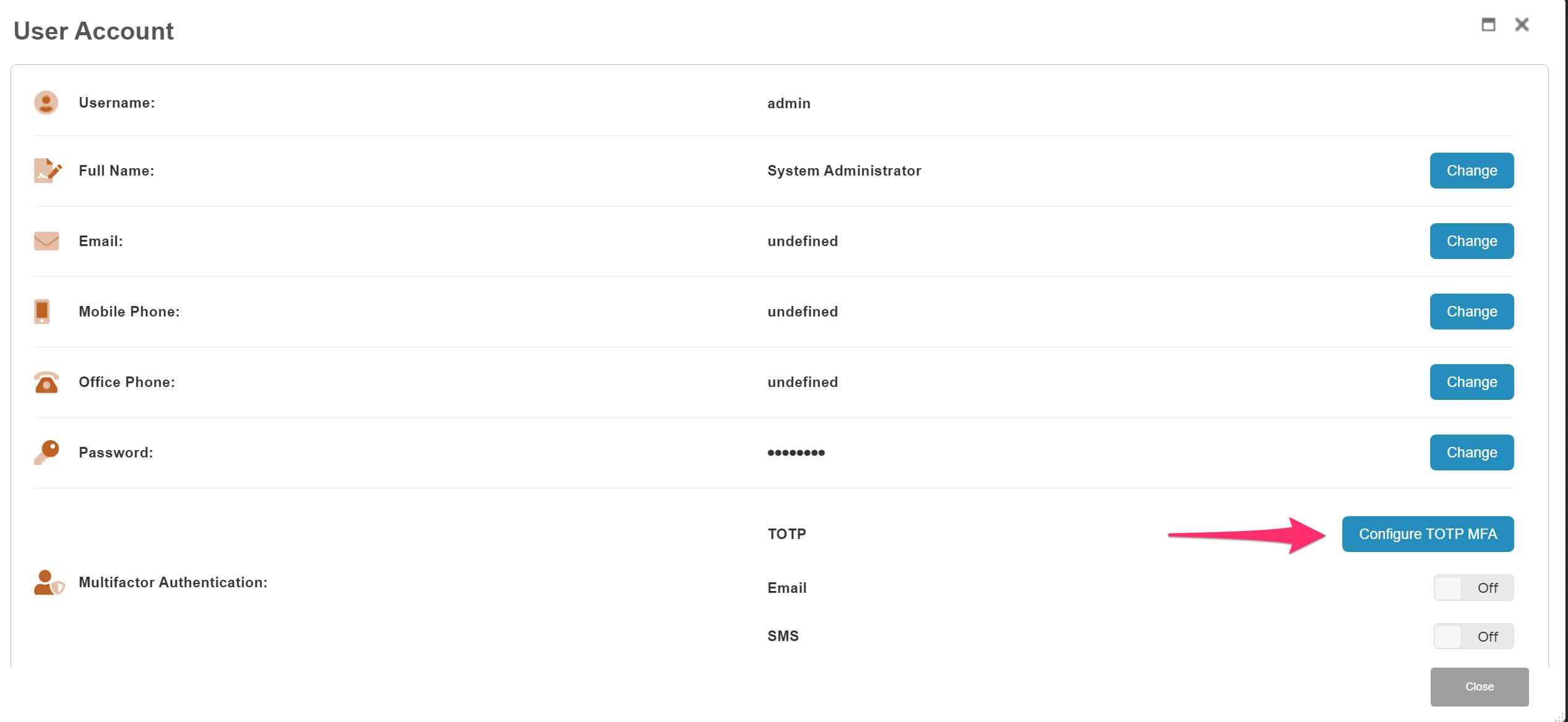
From here select ‘Configure TOTP MFA’ but you will also notice that we can also configure a user’s email address and mobile phone number if other authentication methods are used.
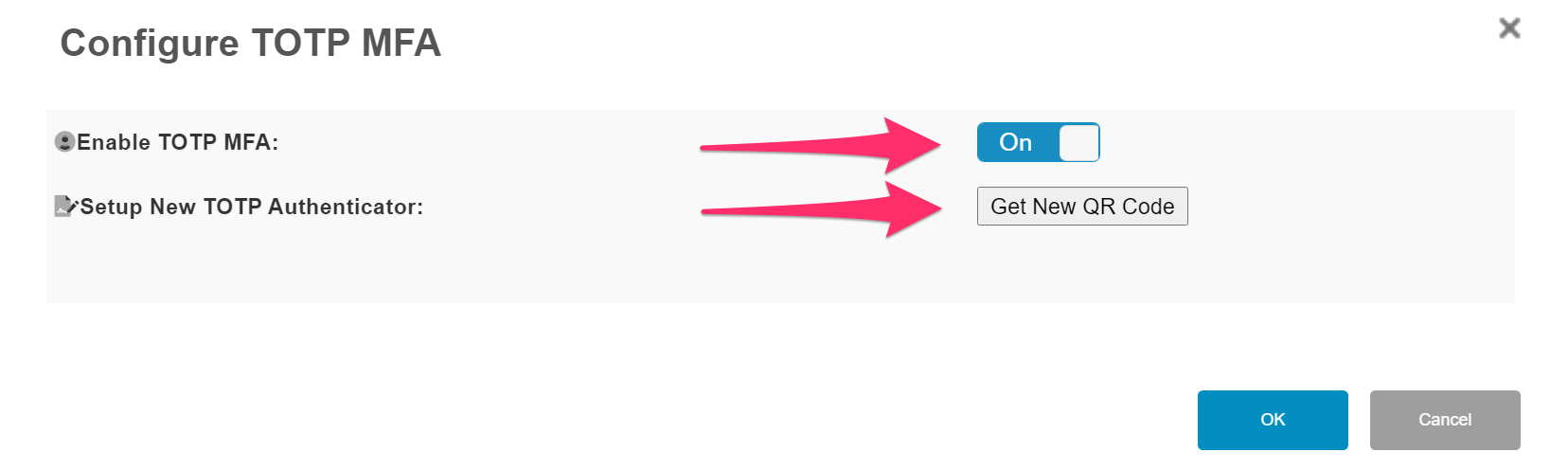
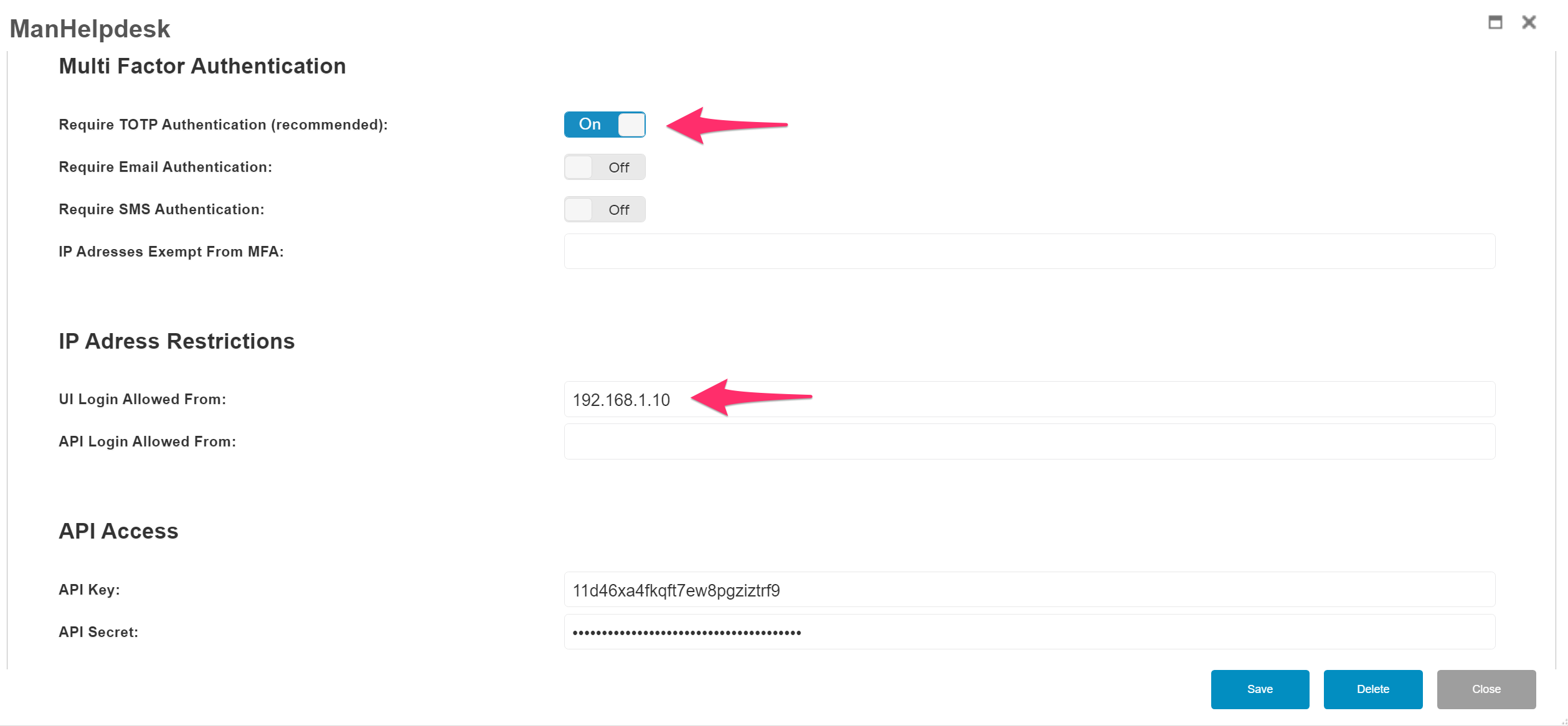
Next enable ‘TOTP MFA’ and then ‘Get New QR Code’
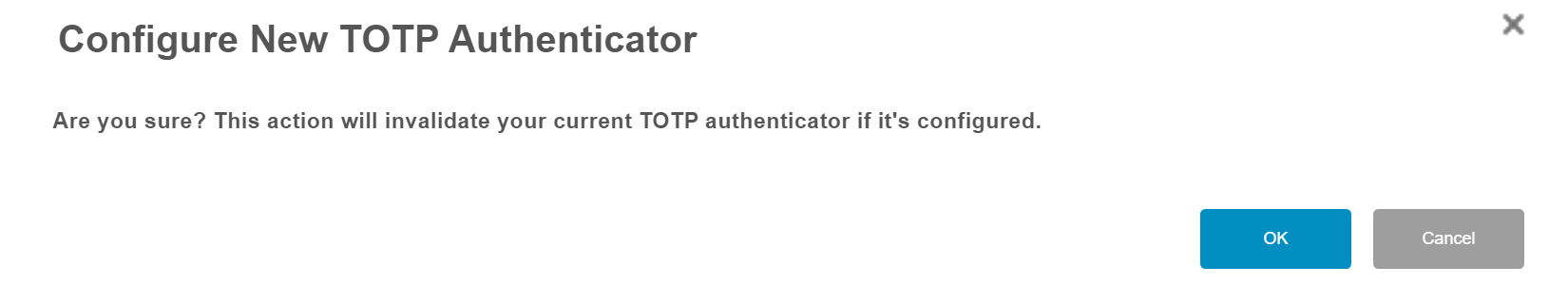
If you’ve previously configured TOTP MFA then you will see the warning below, so select ‘OK’ to continue.
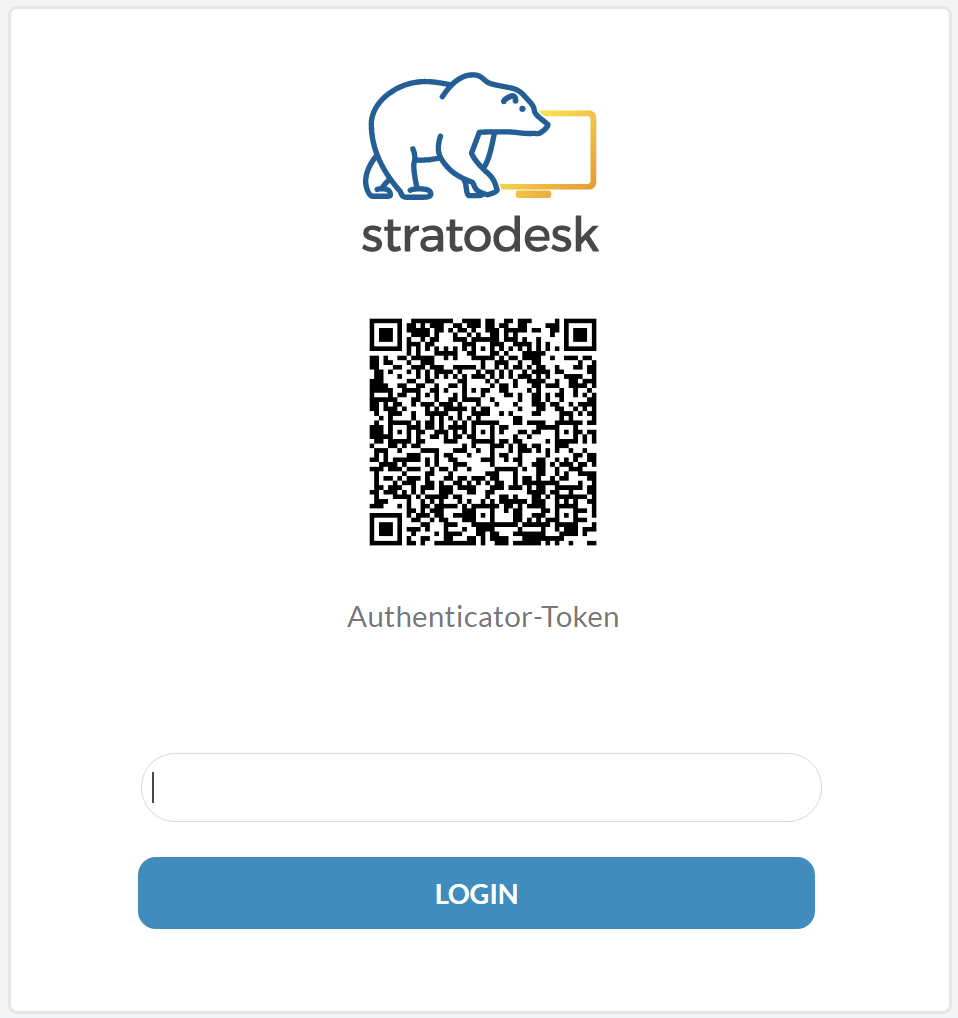
Using your favorite authenticator application, select ‘Add Account’ and scan the QR code on the screen.
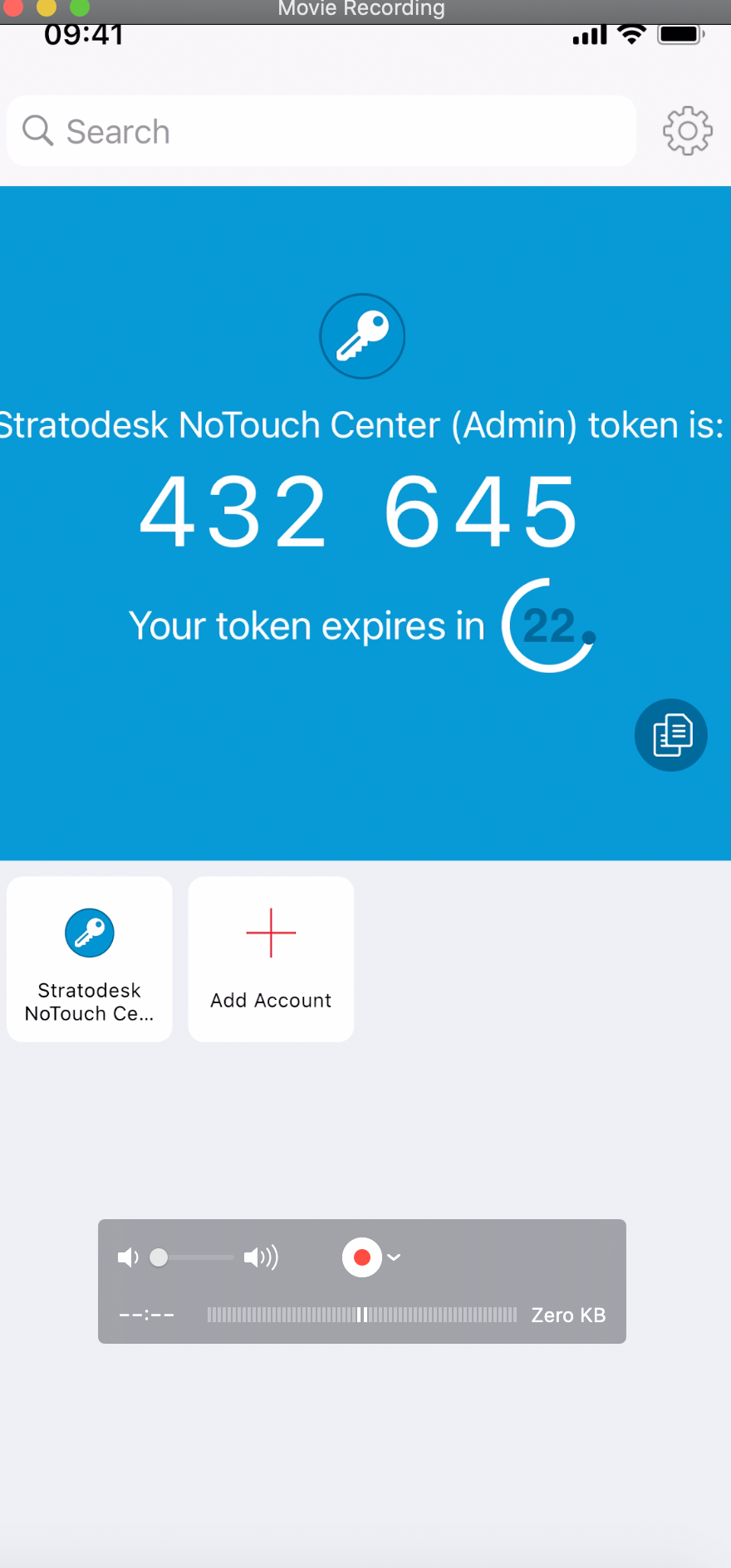
Once the QR code has been scanned, you can click OK to close the screen, and your TOTP application should be showing something similar to the image below showing a random 6-digit token that expires every 30 seconds.
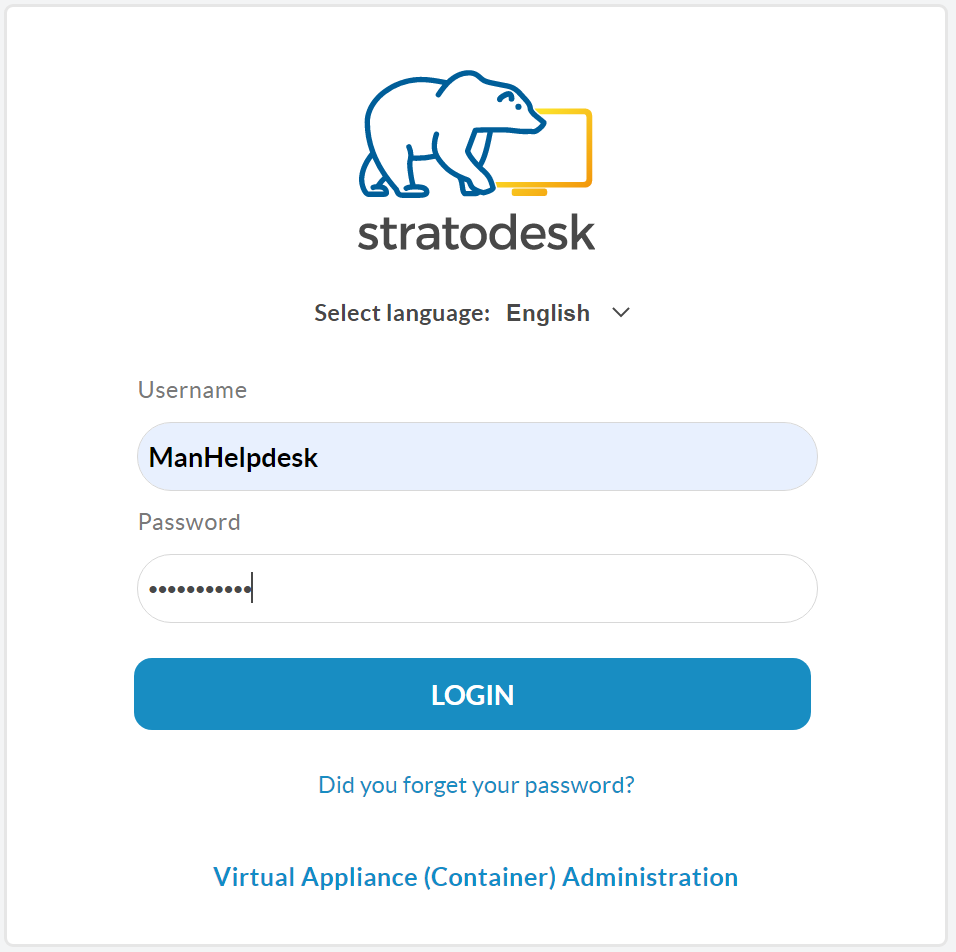
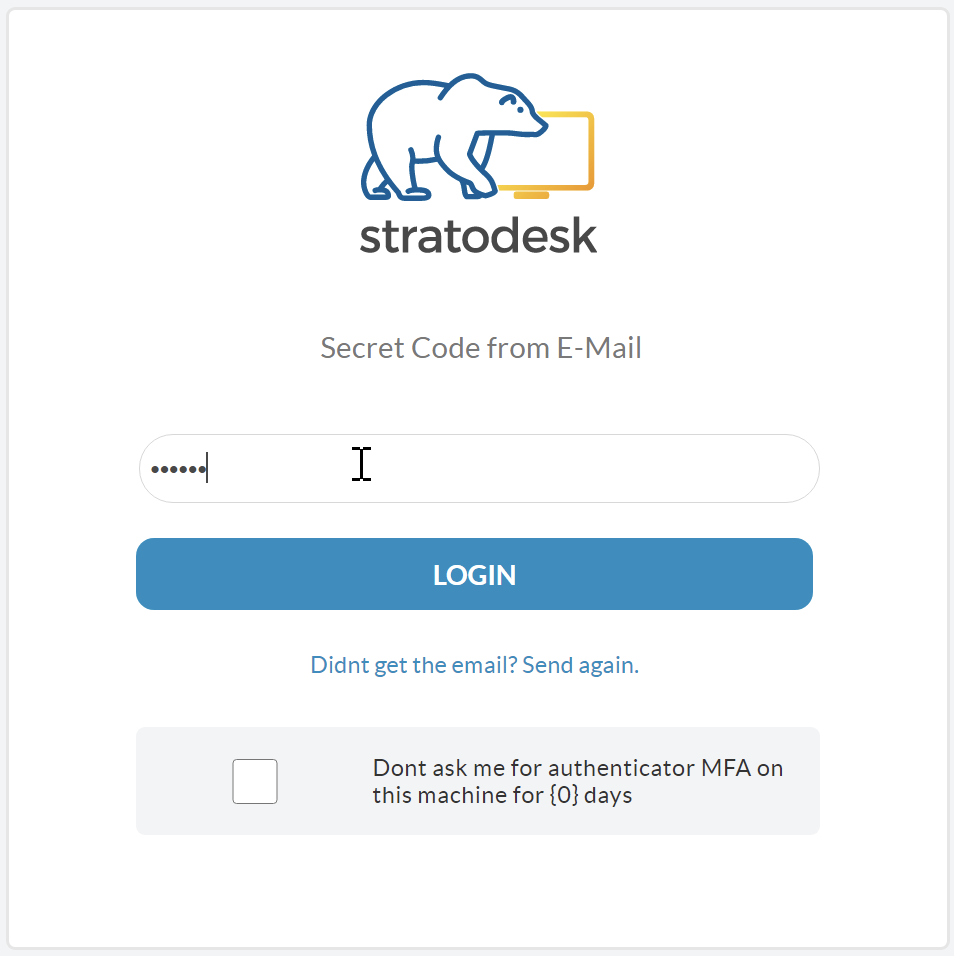
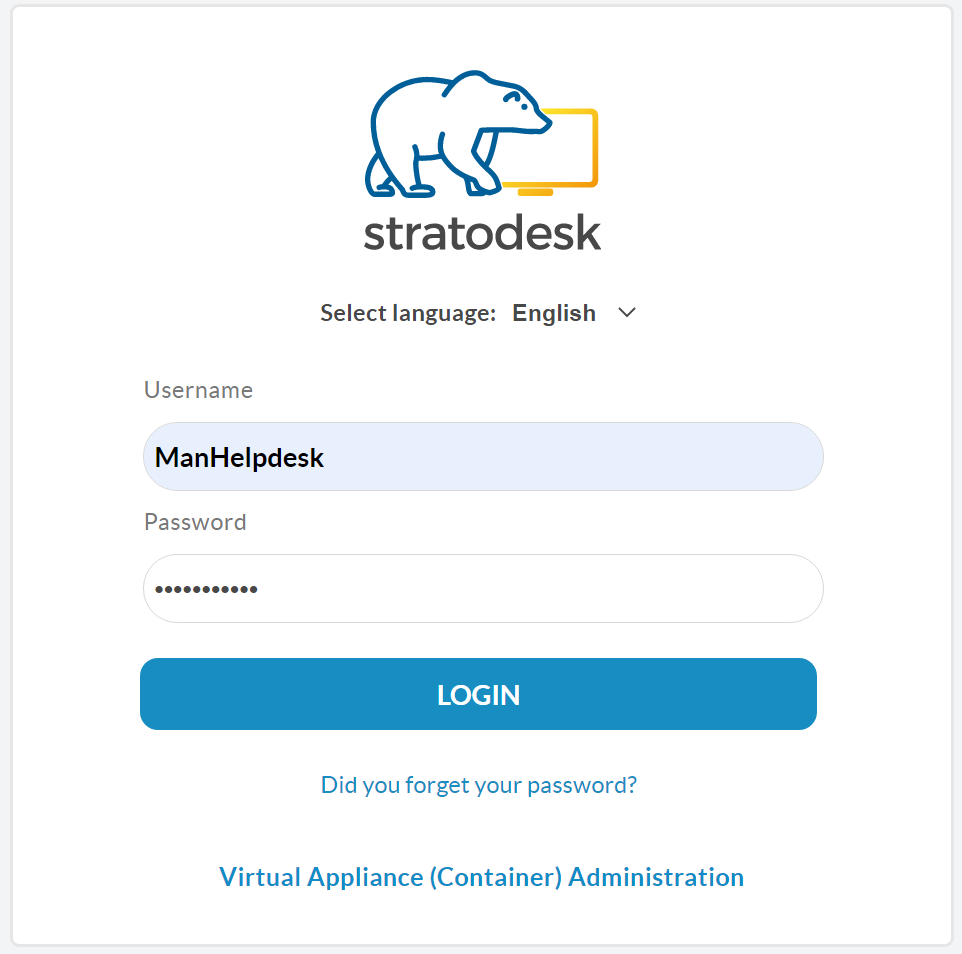
The next time you try to log into NoTouch Center enter your username & password as you would do normally and select the login button.
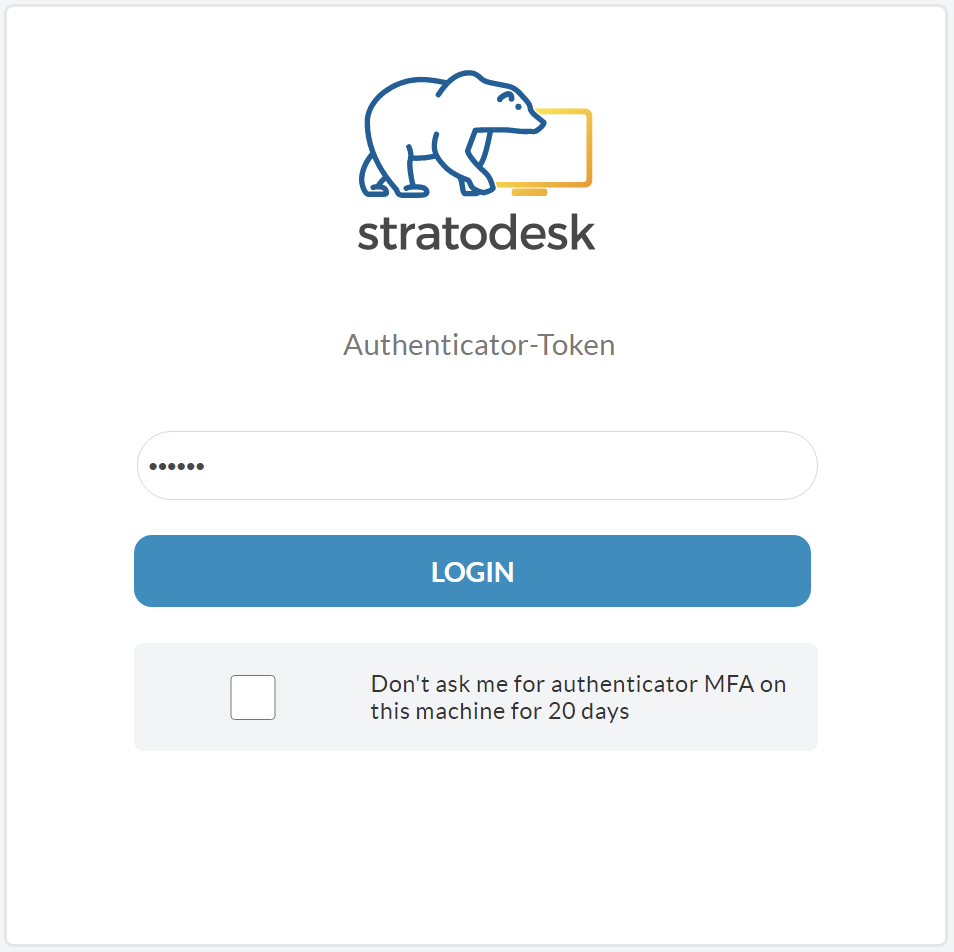
If you’ve configured TOTP authentication correctly, you should then be prompted to provide an authentication token that you can get from the app you configured previously and then click login. If you wish to suppress this for some time, then of course you can do this although we don’t recommend it.
How to Configure MFA for non-Admin Users
If you’ve created additional users in NoTouch Center then MFA is configured in a slightly different way. This time select the user’s icon to go to the user’s screen and select the account or accounts that you want to enable MFA to.
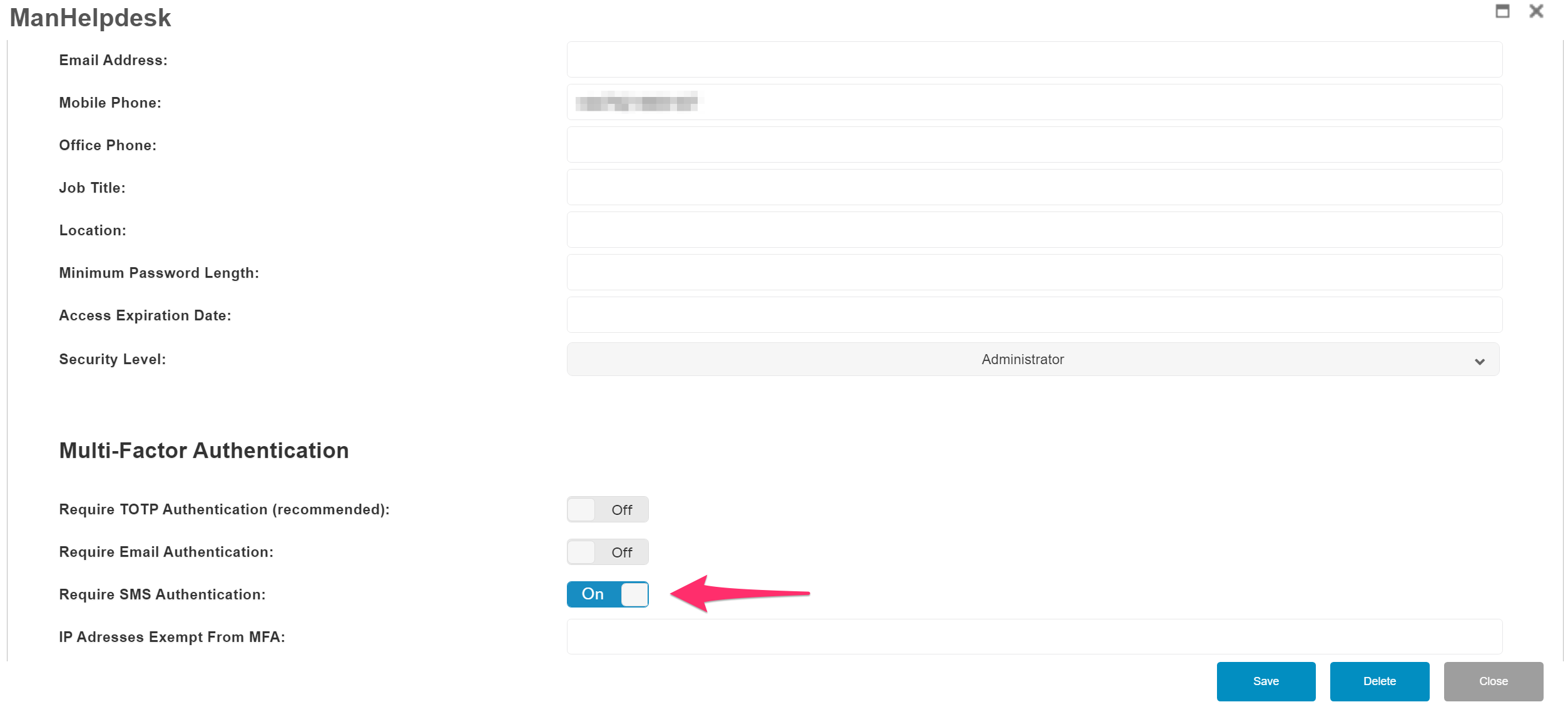
On the next screen select the account you wish to configure and add any additional account information for the user like email address & mobile phone number then scroll to the MFA parameters and enable TOTP authentication and then click ‘save’ & ‘close’
For added security, you can also restrict the IP addresses that can access the NoTouch Center.
When the user logs in for the first time, they will be prompted to set up their authenticator app by scanning the QR code on the screen and can then enter the appropriate authenticator token.
Email Based MFA
Stratodesk NoTouch supports email-based MFA which can be configured in two ways, with the first using existing Gmail account credentials.
If the email from which you wish the users to receive MFA messages is a Gmail account, please provide only the username and password. Otherwise, you must configure the SMTP settings below. If both Gmail and SMTP are configured, Gmail settings will take precedence. If you are using Gmail, then please refer to the security guide for Enabling less secure apps to access Gmail which is a requirement for this feature to work.
To use the feature simply provide your Gmail username & password.
You can then test the settings to ensure they are correct, by providing a valid email address and clicking OK.
If the parameters have been configured correctly you will receive a notification confirming that the test email has been sent.
Next check the email account you sent the test email to, to confirm that the test email has been received.
Next, you will need to enable email-based MFA for your users, ensuring you have specified their email address in their account profile and save the settings.
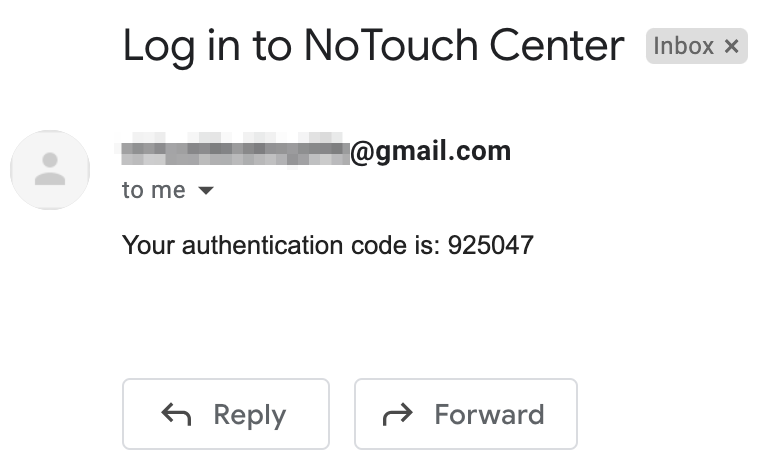
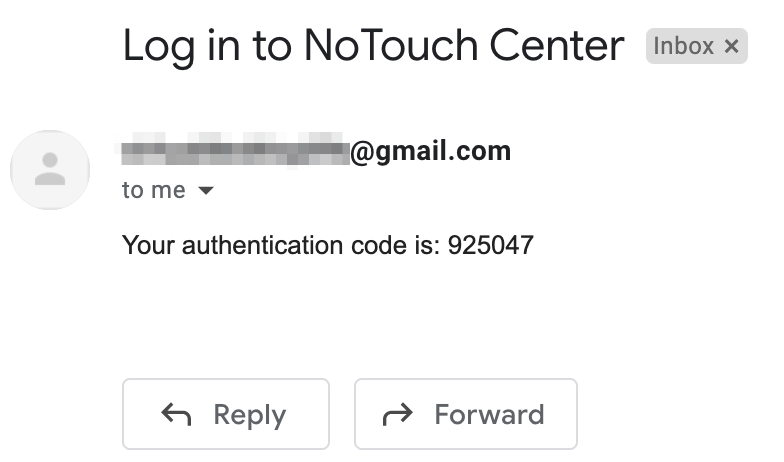
The next time the user logs into NoTouch Center, they should receive an email from NoTouch Center with their 6-digit code and will be able to log in.
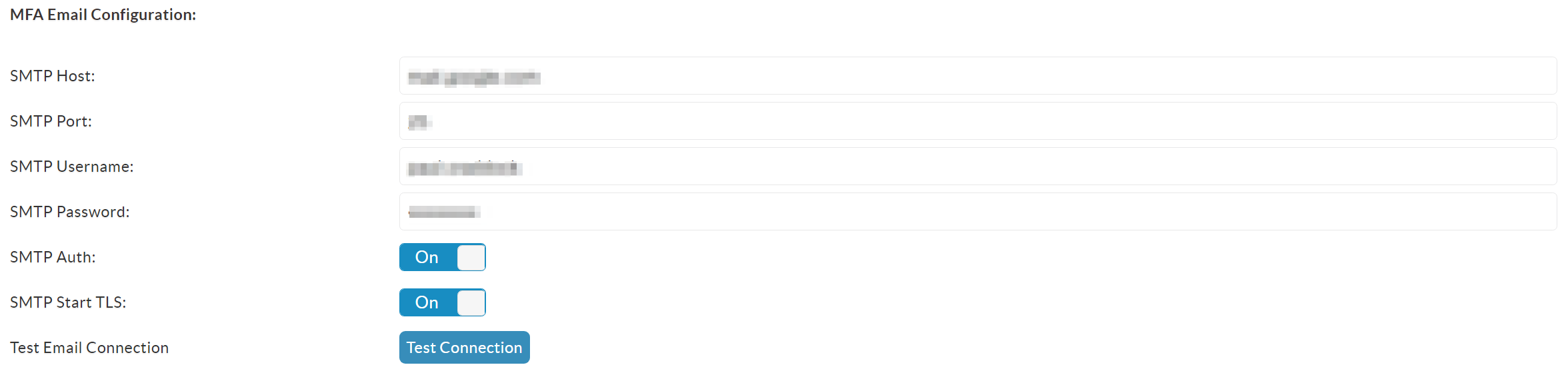
The second option is to use your own SMTP servers, so simply provide the correct credentials based on the requested fields. Your email administrator should have this access easily available. Once configured you should be able to test the connection to verify that they work correctly.
The test process is the same as previously described for setting up Gmail-based MFA. It’s also worth noting that if both Gmail and SMTP are configured, Gmail settings will take precedence.
Text-Based MFA
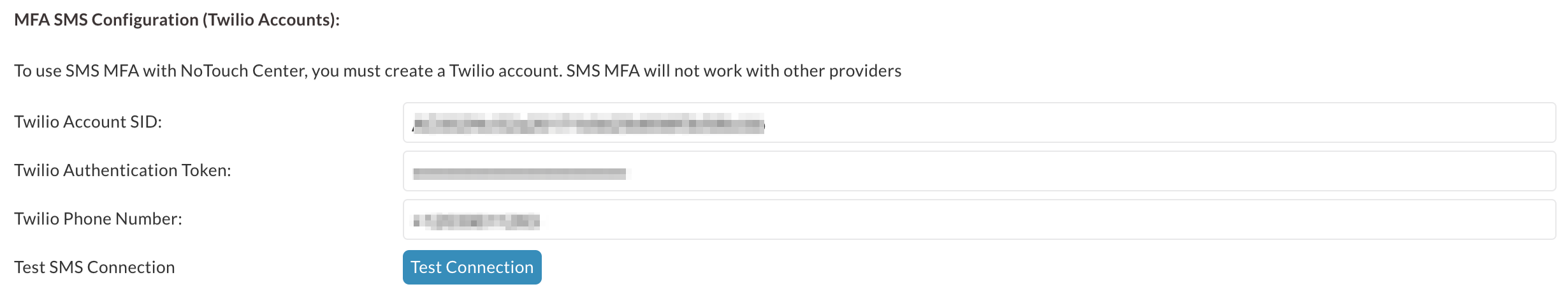
Stratodesk NoTouch supports text-based MFA using the Twilio API, and you will need a Twilio active subscription to use the service. Once your subscription is active, you’ll need to add the following into NoTouch Center via the configuration settings.
Twilio Account SID
Twilio Authentication Token
Twilio Phone Number
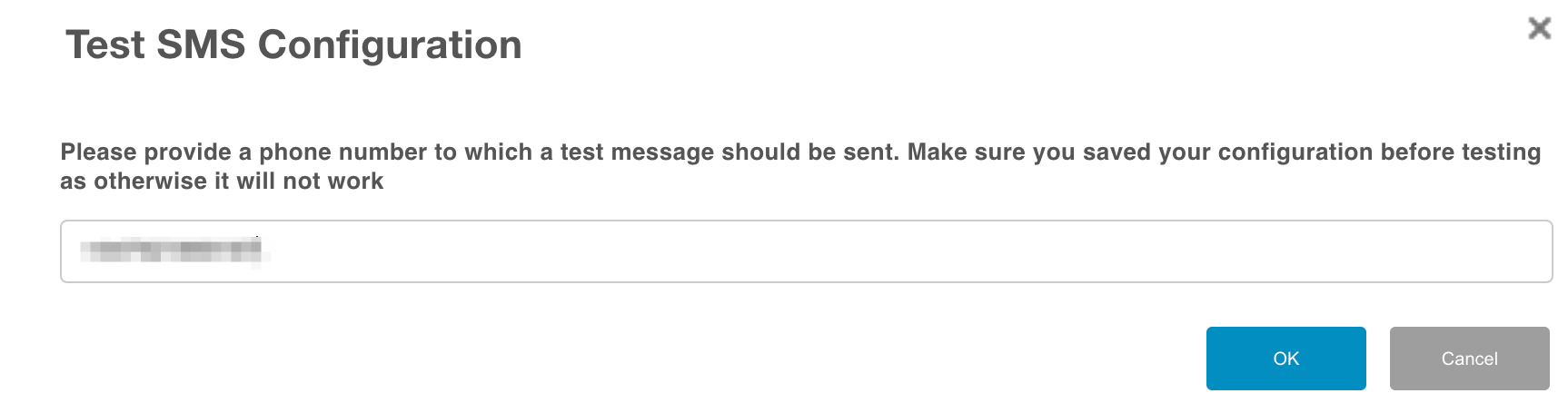
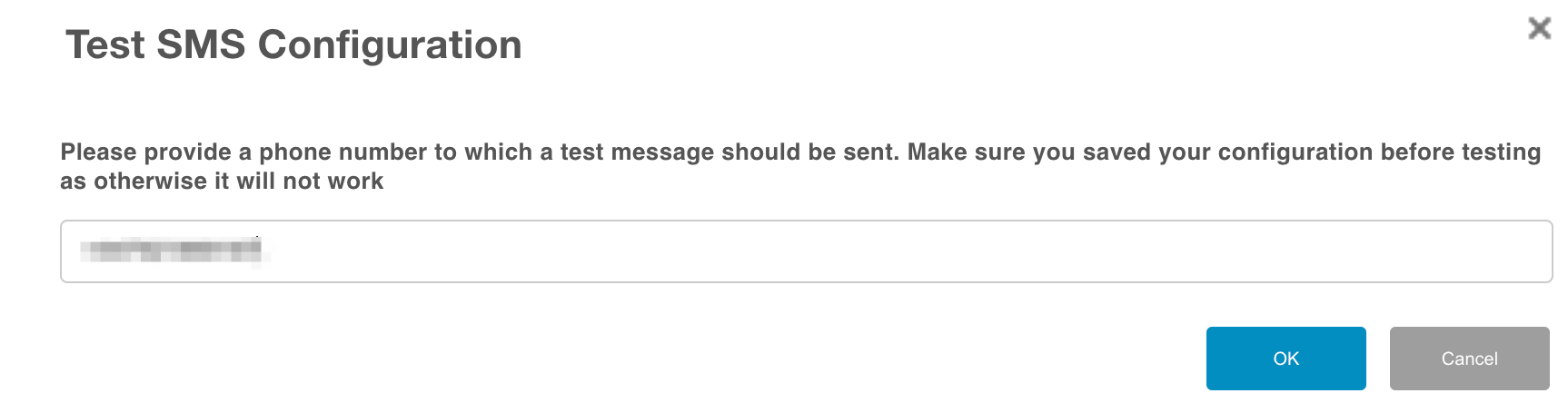
Once you’ve added the parameters, save the settings. You can test these settings by using the ‘Test SMS Connection’ feature.
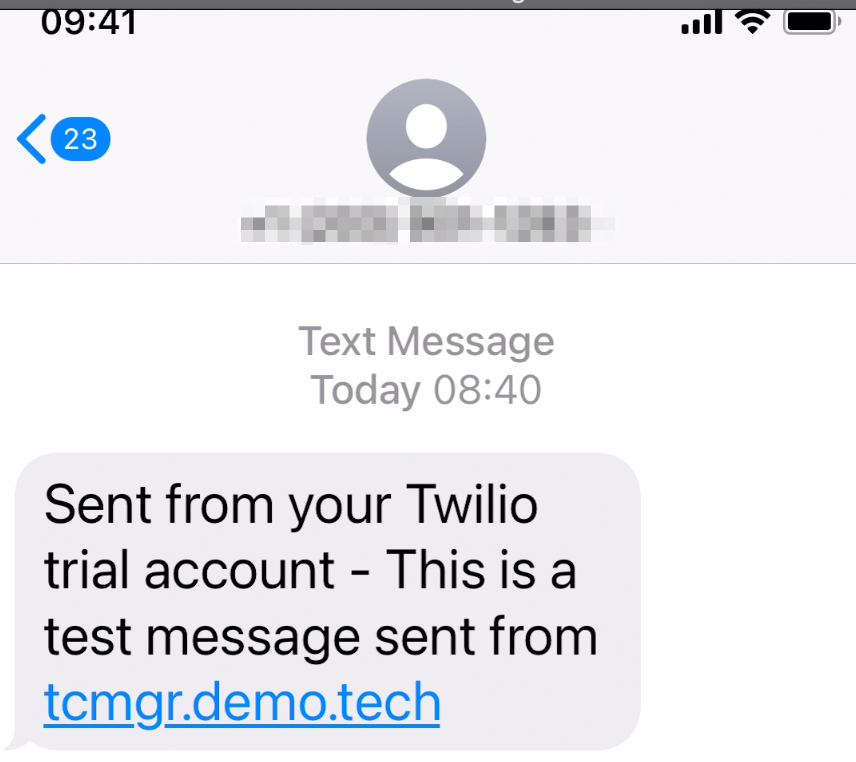
If successful, you should receive a test message as shown below.
Next, you will need to enable SMS-based MFA for your users, ensuring you have specified their mobile number in their account profile.
Once complete save the settings and click close.
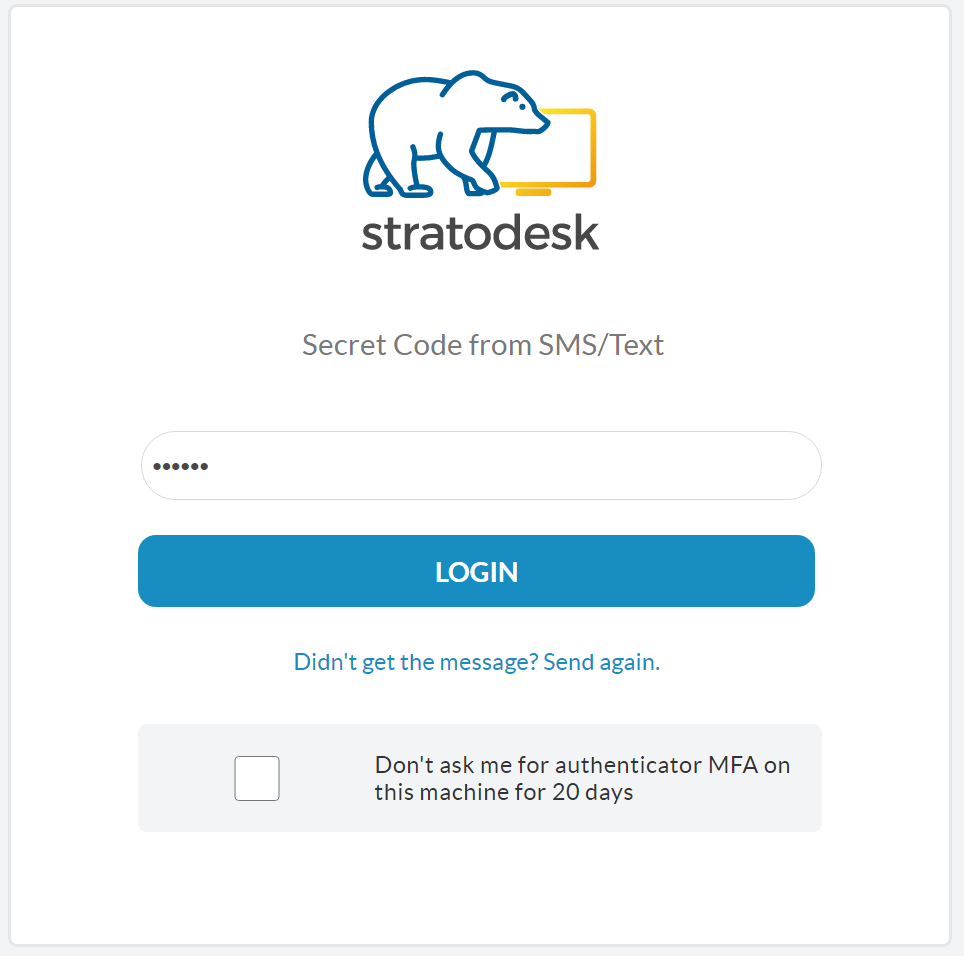
The next time the user logs in they will receive an SMS message with a six-digit one-time passcode.
The user should then enter a six-digit passcode to be authenticated. There’s also the option to suppress MFA from the trusted device for 20 days.